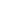I build practical cybersecurity capability across blue, red, and purple team disciplines, with a strong focus on cloud and identity security. By combining attack simulation with defensive monitoring and policy-driven controls, I translate real threats into measurable security improvements using Microsoft's security ecosystem.

Cloud Security Hardening
Implementing Zero Trust, RBAC, and security best practices across Microsoft cloud environments.

Endpoint & Identity Protection
Securing users and devices using Intune, Conditional Access, and identity protection policies.

Security Posture & Monitoring
Improving Secure Score and tuning Defender-based security controls for ongoing protection.
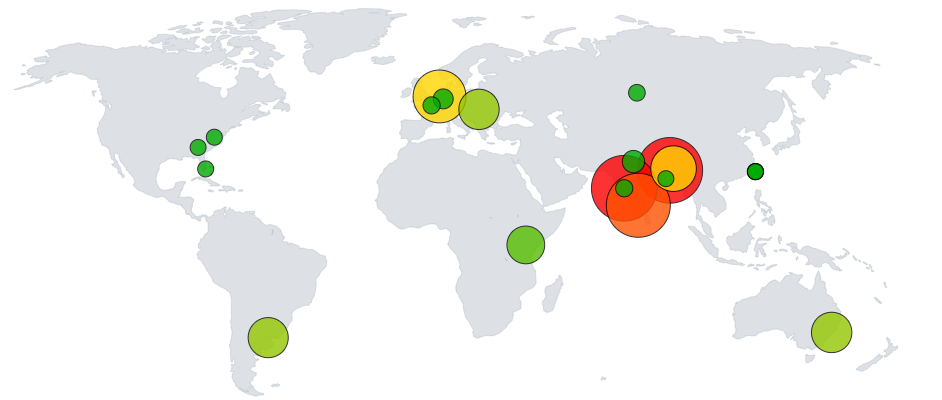
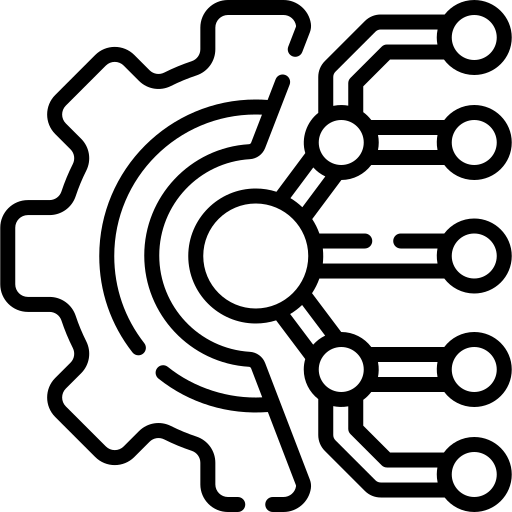
Azure Home Lab
Set up a cloud-based vulnerable machine with firewall rules to simulate attacks, analyse logs in real-time, and visualise global hacking attempts using an IP geolocation world map.

Nmap Automation Tool
Developed a Bash-based Nmap automation tool to streamline network reconnaissance, featuring customisable scan profiles, efficient service detection, and automated output logging for penetration testing workflows.

Penetration Testing Report with Technical Appendix
Conducted a simulated penetration test, documenting vulnerabilities, exploitation steps, and remediation strategies with a detailed technical appendix for deeper insight.
Cisco Packet Tracer: Enterprise Network Design
Designed and configured a secure enterprise-level network in Cisco Packet Tracer, implementing VLAN segmentation, ACLs, and redundancy to simulate real-world network hardening